A few weeks ago, a lead DevOps engineer at a fast-growing SaaS company hit an unexpected wall.
“It used to just work… until we scaled,” the lead noted after their Terraform setup began buckling under the weight of a growing cloud footprint.
Another chimed in:
“We’re spending thousands on infrastructure every week, but we can’t trace it back to who deployed what, or why.”
Sound familiar?
You’re not alone.
Across industries, more teams are quietly hitting their Terraform breaking point. Whether it’s vendor licensing drama, painful state file management, or just the creeping sense that there’s a better way.
In response, a new generation of infrastructure-as-code tools has emerged as reliable Terraform alternatives.
In this post, we’ll walk you through the most promising Terraform competitors today.
As always, we’ll share what sets them apart, what each one actually costs, and which tools innovative engineers, CTOs, and FinOps pros are turning to next.
And when you’re ready to understand, control, and optimize your infrastructure provisioning costs? We’ll show you how CloudZero makes it simple.
Why Switch From Terraform?
Terraform has served thousands of teams well for years. It’s powerful, extensible, and cloud-agnostic. It has been a go-to for codifying infrastructure since the early days of infrastructure as code (IaC).
That said, here are some of the most common reasons teams are seeking Terraform alternatives:
Licensing and vendor lock-in concerns
HashiCorp’s move to a Business Source License (BSL) sparked backlash. Open source advocates and platform vendors, in particular, felt the pinch. Many teams now worry about long-term roadmap control and future usage restrictions (especially true for large-scale or commercial deployments).
Brittle state management
Terraform’s state files are powerful, but they’re also a common source of errors, conflicts, and frustration. Even with remote backends, managing state across teams or environments can be a risky balancing act.
Limited language flexibility
Terraform relies on HCL. Heavily. This is a domain-specific language that’s readable but limited. Teams looking to apply software engineering best practices (testing, loops, abstraction, DRY code) often hit a wall, pushing them toward alternatives like Pulumi or CDK that support real (ahem!) programming languages.
Operational complexity at scale
As deployments grow in size and frequency, Terraform’s plan/apply cycles can become slow and unpredictable. And that means managing dependencies, drift, and concurrent changes across hundreds of modules becomes tedious.
Insufficient collaboration and testing features
CI/CD integration, GitOps support, and pre-deployment testing in Terraform often necessitate workarounds or the use of third-party tooling. This increases fragility and slows down infrastructure delivery for fast-moving teams.
Lacking native cost awareness
Terraform can create resources, but it can’t tell you what they cost, who created them, or if they’re still in use. That visibility gap can often lead to overspending, orphaned resources, and misalignment between engineering and finance.
See also:
Up next, we’ll explore the most viable Terraform alternatives available today.
11 Terraform Alternatives You’ll Want To Explore For Smarter Cloud Resource Provisioning
Whatever the reason, the goal is the same: finding the right balance of flexibility, scalability, and cost efficiency for your infrastructure and team.
For that, consider these top contenders:
1. Pulumi
Pulumi is an infrastructure-as-code platform that lets you define cloud resources using general-purpose programming languages like TypeScript, Python, Go, .NET, and Java. This makes it especially appealing to developer-first teams that want to bring software engineering practices to infrastructure management.
Pulumi pros:
- Uses familiar languages and tooling, including IDEs, unit testing, and package managers
- Strong CI/CD and GitOps compatibility
- Rich multi-cloud support (AWS, Azure, GCP, Kubernetes, and more)
- Type-safe code with support for abstractions and reusability
- Active community and enterprise-grade support
Pulumi cons:
- Higher learning curve for traditional ops teams not familiar with programming
- Complex setups can become harder to onboard new team members into
- Requires managing additional runtime SDKs and dependencies
Pulumi IaC pricing offers a free tier for individual use, with team and enterprise plans starting at $50/user/month.
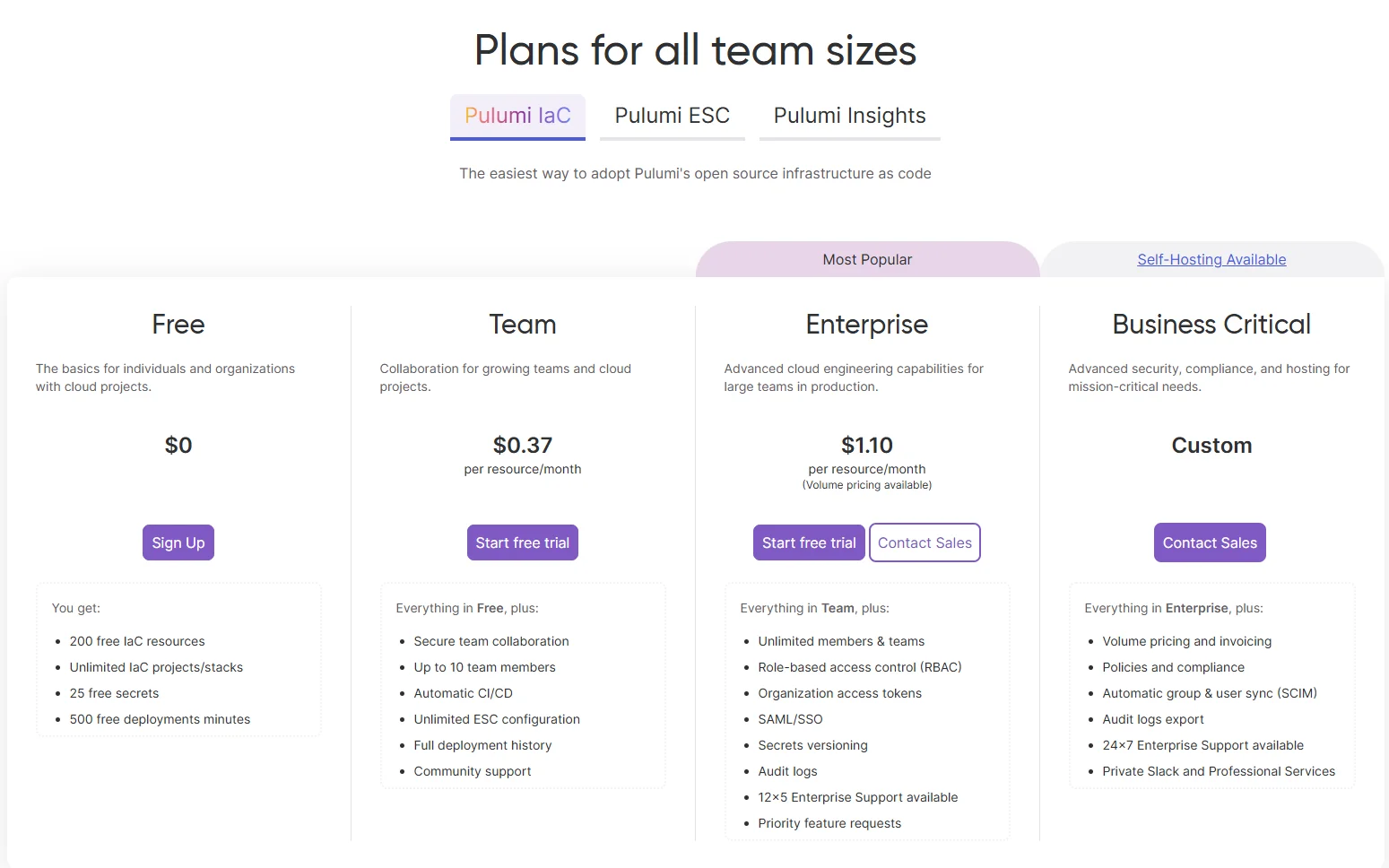
Open-source SDKs and automation APIs are free to use, but advanced features like policy enforcement and audit logs require a paid plan.
Pulumi is best for engineering-heavy teams that want to treat infrastructure as real code, with all the flexibility, automation, and modularity of a modern software stack.
2. OpenTofu (formerly OpenTF)
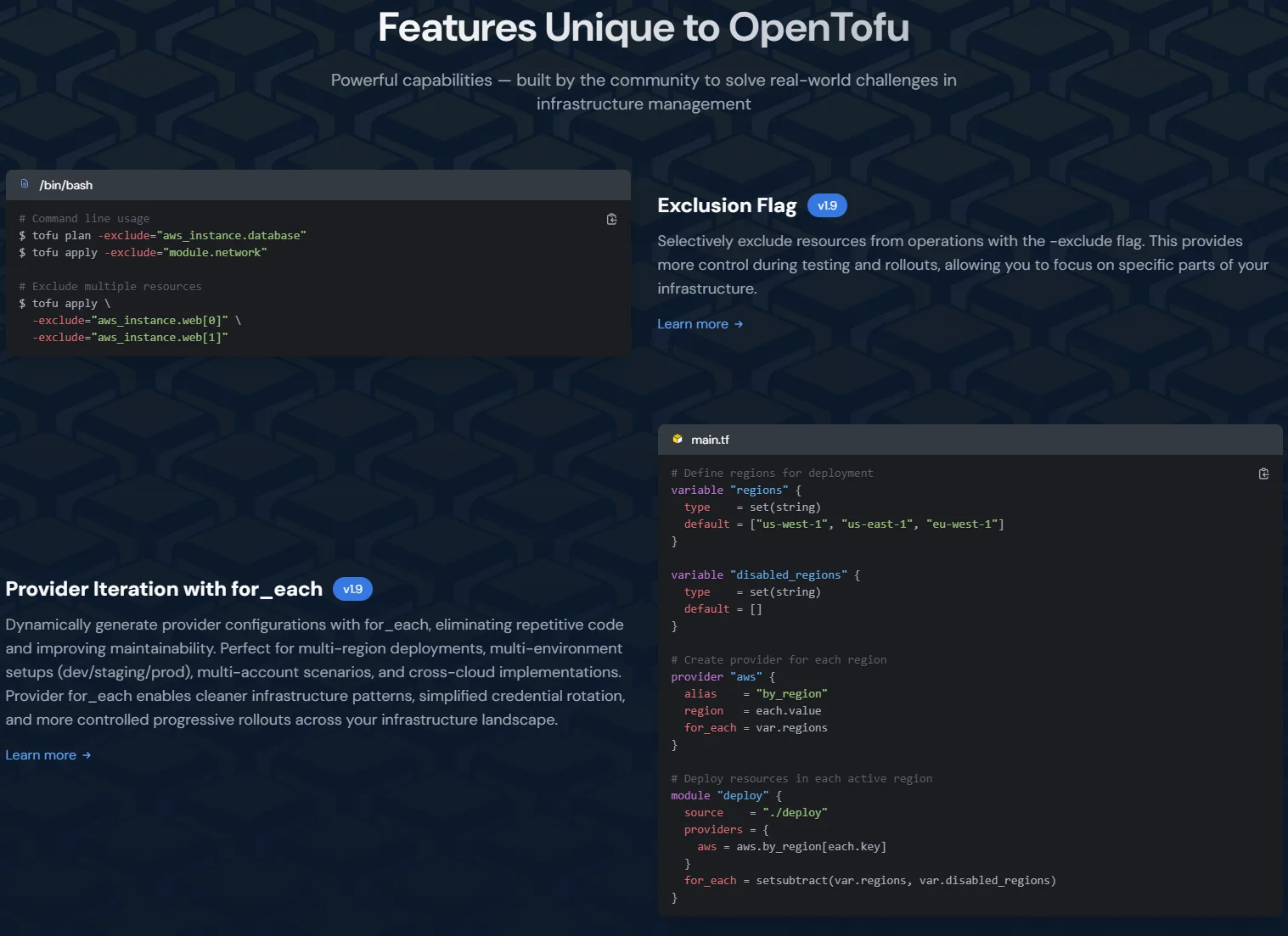
OpenTofu is a community-driven, open-source alternative to Terraform, created in response to HashiCorp’s licensing changes. Use it if you want a replacement that’ll remain fully open and community-governed while also being compatible with the Terraform ecosystem.
OpenTofu pros:
- Fully open source under the MPL 2.0 license
- Backed by the Linux Foundation and growing vendor support
- Compatible with existing Terraform modules and workflows
- No commercial restrictions, so it’s ideal for platforms and tooling providers
- Rapid community adoption and development momentum
OpenTofu cons:
- Still catching up in terms of ecosystem maturity and stability
- Some organizations may hesitate to switch until the project fully matures
- The governance model is promising but still in its early stages
OpenTofu pricing: Free and open source, with no licensing fees or usage restrictions.
It is best for teams that want Terraform’s capabilities without the licensing baggage. Also, consider it if you are investing in long-term open-source infrastructure stacks.
3. Crossplane
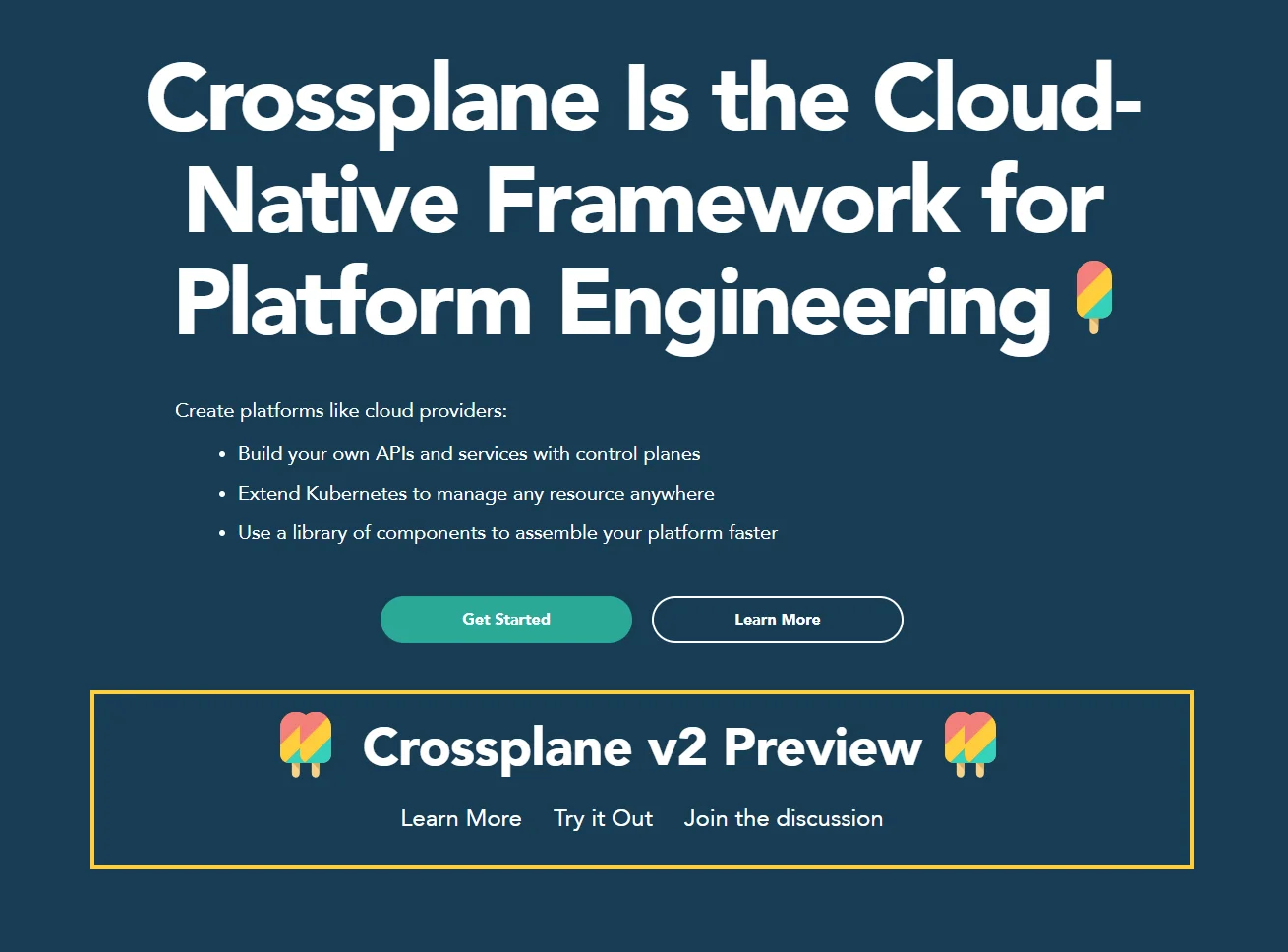
Crossplane is a Kubernetes-native control plane. You can use it to provision and manage cloud infrastructure using Kubernetes APIs and declarative YAML. It lets you compose infrastructure like you would applications.
Crossplane pros:
- Seamless integration with Kubernetes and GitOps workflows
- Policy-based resource composition using XRDs and compositions
- Multi-cloud orchestration through standard Kubernetes tooling
- Strong separation of concerns for platform teams vs app teams
- No state files to manage
Cons:
- Requires a strong Kubernetes foundation
- It can be overkill for small teams or non-Kubernetes use cases
- The learning curve for non-Kubernetes-native users can be quite substantial
Crossplane pricing: Open source and vendor-neutral. Note that commercial support is available from companies like Upbound (creators of Crossplane IaC) and Nirmata.
Use Crossplane if you are a Kubernetes-centric organization looking to unify app and infrastructure management under one declarative model.
4. AWS CloudFormation
CloudFormation is Amazon’s native infrastructure-as-code service. It helps define AWS resources using JSON or YAML templates. As an AWS-first option, it’s deeply integrated into the ecosystem and supports nearly every AWS service out of the box.
CloudFormation pros:
- Native support for all AWS resources
- Seamless integration with AWS Identity and Access Management (IAM), Config, CloudTrail, and Control Tower
- Drift detection and rollback support
- Built-in change sets for safer deployments
- No additional tooling or runtime needed
Cons:
- Limited to AWS. No support for multi-cloud environments
- JSON/YAML templates can be verbose and difficult to reuse
- Poor abstraction and modularity compared to alternatives like CDK or Pulumi
CloudFormation pricing: Free to use. You only pay for the AWS resources provisioned.
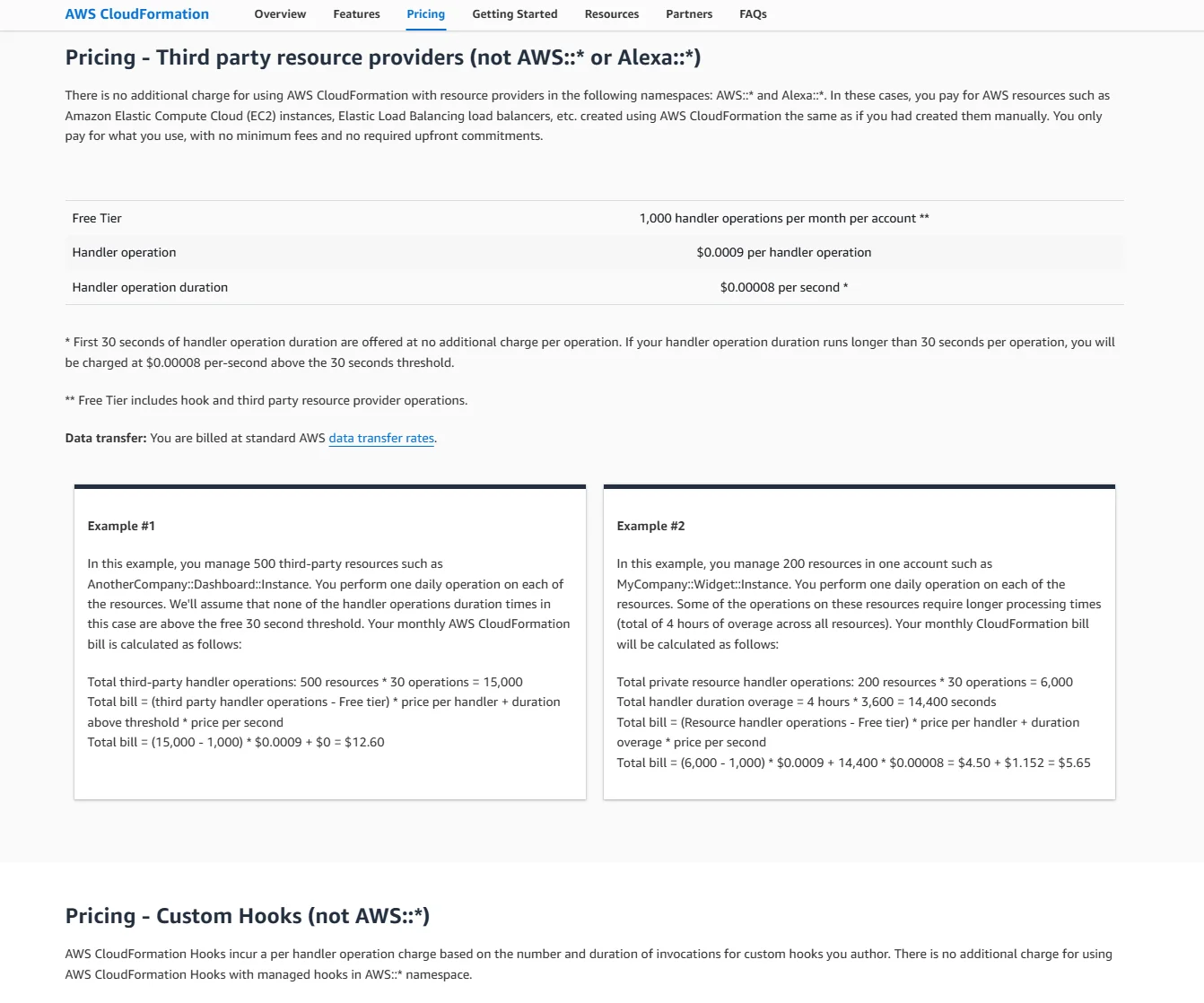
CF is best for AWS-only teams that want a secure, deeply integrated IaC solution without introducing third-party tooling.
5. AWS Cloud Development Kit (CDK)
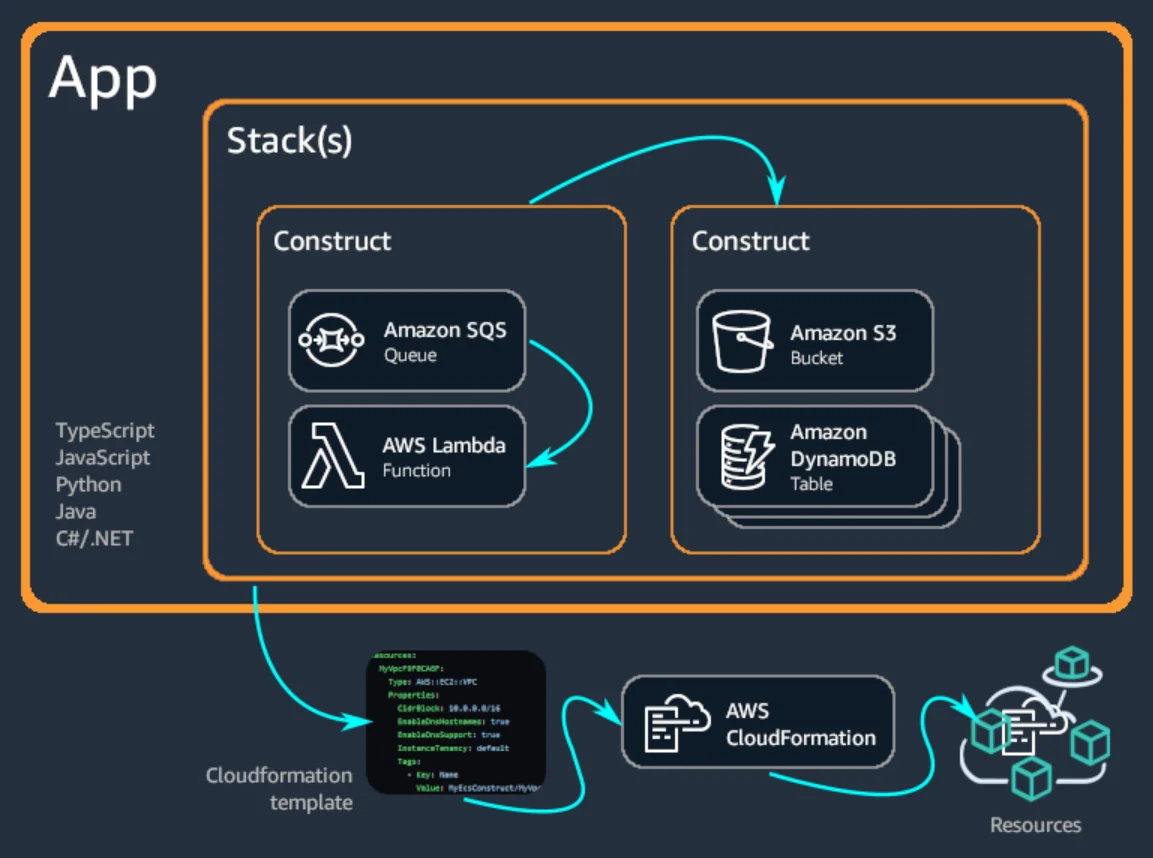
When you use AWS CDK as IaC, you can define cloud infrastructure using popular programming languages like TypeScript, Python, Go, Java, and C#. It compiles to CloudFormation templates behind the scenes, combining developer experience with native AWS power.
AWS CDK pros:
- Use real programming languages with strong type safety
- Higher-level constructs (L2 and L3) speed up development
- Reuse logic, build abstractions, and write tests
- Strong AWS support and official backing
- Easily integrates into existing developers’ workflows
AWS CDK cons:
- Still AWS-specific, so it’s missing native multi-cloud capabilities
- CDK-generated CloudFormation stacks can be harder to troubleshoot
- Some abstraction layers hide implementation details, which may confuse ops teams
AWS Pricing: Like CloudFormation, it is free to use; you pay only for provisioned AWS resources.
AWS CDK is ideal for developer-first AWS teams looking for modern infrastructure workflows, reusable components, and software engineering-level control over infrastructure.
6. Bicep (for Azure)
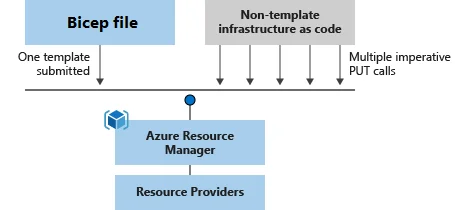
Bicep is a domain-specific language (DSL) from Microsoft that simplifies writing Azure Resource Manager (ARM) templates. It replaces verbose JSON with a cleaner, modular syntax while remaining 100% compatible with ARM.
Bicep pros:
- Clean, readable syntax compared to raw ARM templates
- Supported and maintained by Microsoft
- Native Azure integration and support in Azure CLI and Visual Studio Code
- Transparent transpilation to ARM JSON (for auditing and compliance)
- Modular and reusable components (modules)
Bicep cons:
- Azure-only. Bicep is not suitable for multi-cloud environments
- Limited ecosystem maturity compared to Terraform or Pulumi
- Still evolving, so some advanced features may lag behind
Bicep Iac pricing: Free to use. It is available as an open-source project under the MIT license.
It is ideal for you if you are deeply invested in Azure and want a simpler, more modern IaC experience without leaving the Microsoft ecosystem.
Now, for this next batch of tools, we’ll focus on config-centric tools, commercial governance platforms, and wrappers that improve Terraform without replacing it entirely (if ditching Terraform proves trickier than expected).
7. Ansible
Ansible is an open-source automation platform that can handle infrastructure provisioning, configuration management, and application deployment. Unlike declarative tools like Terraform, Ansible uses an imperative, task-based model. It is ideal for hybrid and dynamic environments.
Ansible pros:
- Simple, human-readable YAML syntax
- Agentless (it communicates over SSH/WinRM)
- Great for configuring servers after provisioning
- Broad support for cloud, on-prem, and networking devices
- Large collection of reusable roles and playbooks
Cons:
- Not designed specifically for infrastructure provisioning
- No state management, so it could be tough to track or reverse changes
- Can be less predictable in idempotency compared to declarative tools
For pricing, Ansible is open source. However, the Red Hat Ansible Automation Platform is available for enterprise use with support and governance features.
Ansible is best for ops-heavy teams managing hybrid infrastructure and complex post-provisioning config workflows. It is especially ideal when consistency and repeatability matter more than drift detection.
8. Chef, Puppet, and SaltStack

These classic configuration management tools pioneered infrastructure automation before Terraform was born. Although not direct Terraform replacements, they can provision resources (with extensions) and are still used in many enterprise and hybrid cloud environments.
Pros:
- Mature and battle-tested in enterprise environments
- Strong at enforcing configuration drift correction
- Detailed control over system state and compliance
- Good for managing long-lived, on-prem workloads
Cons:
- Steep learning curves and dated DSLs
- Require agents or daemons
- Limited support for modern IaC practices and workflows
- Declining popularity compared to newer tools
Pricing: Open-source options are available. Enterprise pricing depends on the specific vendor, such as Progress for Chef and Perforce for Puppet.
Best for: Legacy-heavy organizations with strict compliance needs or deeply embedded infrastructure that can’t be easily modernized.
9. Env0, Spacelift, and Scalr (commercial IaC governance platforms)
These platforms don’t exactly replace Terraform. Instead, they supercharge it. Env0, Spacelift, and Scalr offer automation, collaboration, governance, and policy-as-code layers on top of Terraform (and other IaC tools). Think of them as Terraform’s missing enterprise UI.
Pros:
- RBAC, audit trails, and cost policies
- Built-in CI/CD pipelines for IaC
- Terragrunt, Pulumi, and Crossplane support
- Great for large orgs with compliance or security mandates
- Support cost visibility, drift detection, and auto-cleanup
Cons:
- Added cost on top of Terraform
- Requires integration and a learning curve
- Some lock-in, depending on the vendor
Pricing varies:
- Env0 pricing: Starts with the free tier, then the team and enterprise tiers
- Spacelift pricing: Free for individuals, paid for teams
- Scalr IaC pricing: Per-seat enterprise pricing
Best for: Enterprises scaling infrastructure as code across teams that need policy enforcement, visibility, and better collaboration without ditching Terraform.
10. Terragrunt
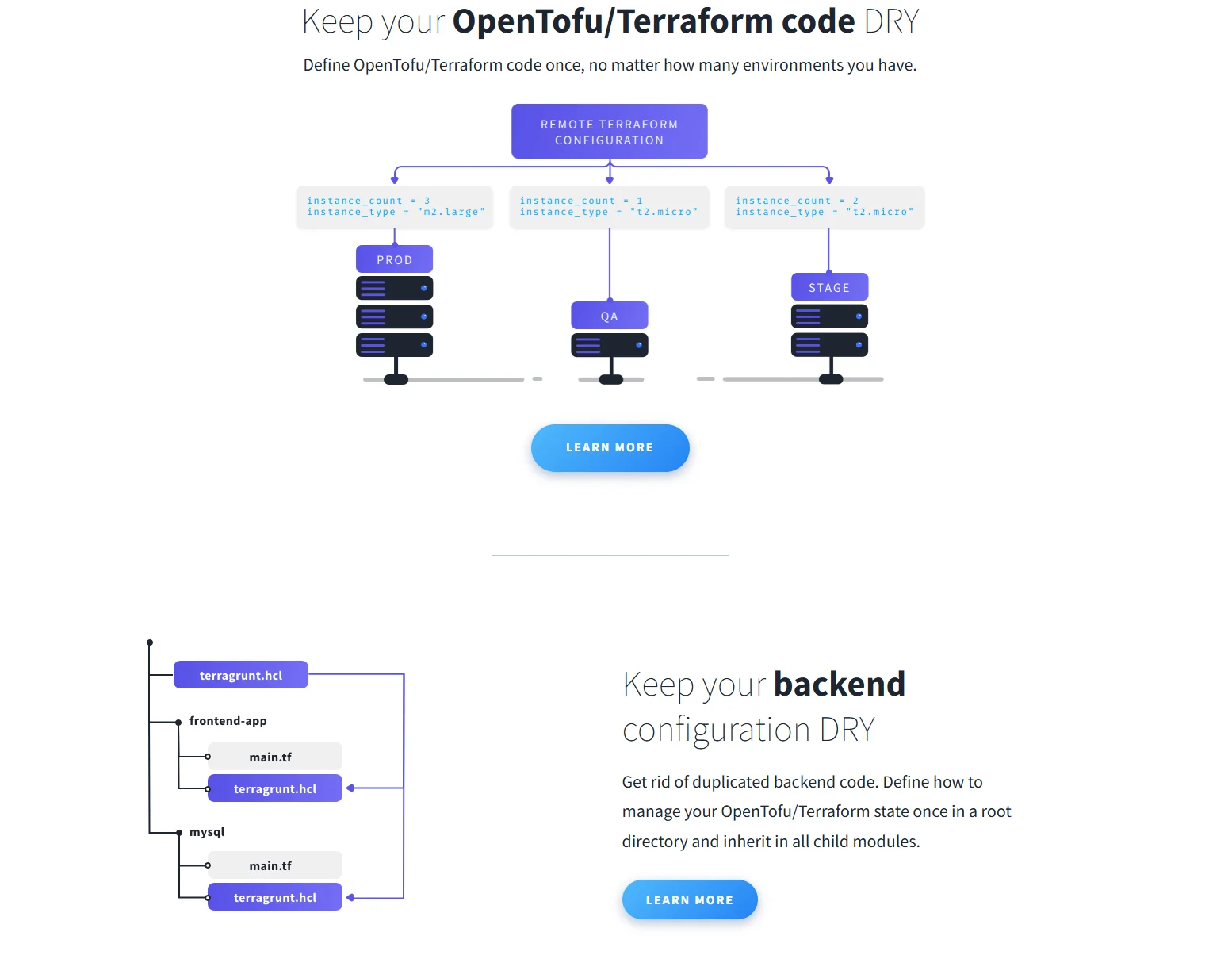
Terragrunt is a lightweight wrapper for Terraform that simplifies the management of multiple environments and modules. Like the group above, it doesn’t replace Terraform, but improves it.
Terragrunt pros:
- Encourages DRY (Don’t Repeat Yourself) Terraform
- Handles dependency chains and remote state management
- Easy multi-environment orchestration
- Ideal for mono-repos or repo-per-env setups
- Works with all Terraform providers and modules
Terragrunt cons:
- Adds another layer of abstraction
- It may be overkill for small teams or simple projects
- Can introduce complexity if misconfigured
Terragrunt pricing includes a free and open source (Apache 2.0) license.
Terragrunt is ideal for you if you want to simplify large, multi-environment setups without having to switch tools. It is especially good in fast-growing infrastructure environments.
11. CUE (Configure, Unify, Execute)
CUE is a newer configuration language that combines data validation, configuration, and templating into one system. It’s not an IaC tool by itself. But, it’s gaining traction as a powerful alternative to JSON or YAML for defining infrastructure and app config in a scalable and reusable way.
CUE pros:
- Powerful typing, constraints, and schema validation
- Ideal for generating consistent config across tools (e.g., Kubernetes, Terraform, Helm)
- Great for building internal platforms and CI/CD pipelines
- Helps reduce config drift and inconsistencies
Cons:
- Not a standalone provisioning tool
- Still early in its adoption curve
- Smaller community and limited native IaC support
CUE pricing: Free and open source.
Configure, Unify, Execute is best for platform engineering teams building internal developer platforms, config pipelines, or advanced templating engines for infrastructure and applications.
With so many options on the table, the question becomes: how do you choose the right Terraform alternative for your architecture, team, and long-term goals?
How To Evaluate Terraform Alternatives For Your Use Case
Some alternatives to Terraform prioritize developer experience. Others focus on multi-cloud compliance, GitOps integration, or policy enforcement at scale.
Here are the key criteria to consider when evaluating what’s next for your infrastructure as code (IaC) strategy:
Language preferences and team skill set
Some tools, like Pulumi and CDK, support general-purpose programming languages like TypeScript and Python. These are perfect for engineering-driven teams who want to apply software development best practices. Others (like Bicep, YAML-based tools, or Crossplane) stick with declarative syntax, which may suit ops teams or compliance-heavy orgs.
Cloud platform support
Cloud-native tools like CloudFormation, CDK, and Bicep are powerful, but vendor-specific (vendor lock-in, anyone?). If you’re running workloads across AWS, Azure, GCP, or Kubernetes, you’ll want a platform-agnostic solution (like Pulumi, Crossplane, or OpenTofu).
State management and deployment complexity
How your team manages infrastructure state (and drift) matters. Tools like Terraform and OpenTofu rely on state files. Crossplane avoids them entirely. Terragrunt helps simplify state across environments. So, you’ll want to choose based on the complexity of your deployments and the need for reliability in automation.
Collaboration, CI/CD, and Policy-as-Code
Look for tools that integrate with your CI/CD pipeline, offer access controls, and support policy-as-code. This becomes critical as your team scales. In that case, governance platforms like Spacelift or Env0 can help manage shared environments and enforce controls across your organization.
Cost awareness and visibility
Provisioning tools rarely answer one of the most important questions you’ll certainly have: What is this infrastructure costing us and why?
Provisioning cloud resources is easy. Knowing what they cost, who created them, and whether they’re still worth it? Not so much.
That’s where platforms like CloudZero step in by connecting your cloud resource usage to cost and business outcomes in real time. How?
Take The Next Step: Bring Cloud Cost Intelligence To Your IaC
You’re rethinking Terraform, and that’s a smart move. But if you can’t see the cost of what’s being deployed, or tie it back to the teams, product features, or customers driving your spend, the risk of waste and misalignment stays high.
Even the best Terraform alternative won’t tell you which services are driving up your bill, or help your team stay accountable for what they deploy.
CloudZero does.
While your IaC tool shows you what gets deployed, CloudZero shows you what it costs, who’s responsible, and how to optimize it.
You get real-time, engineering-friendly cost insights, broken down by environment, team, deployment, or feature, so you can prevent surprises and prove ROI with every release. Picture this:
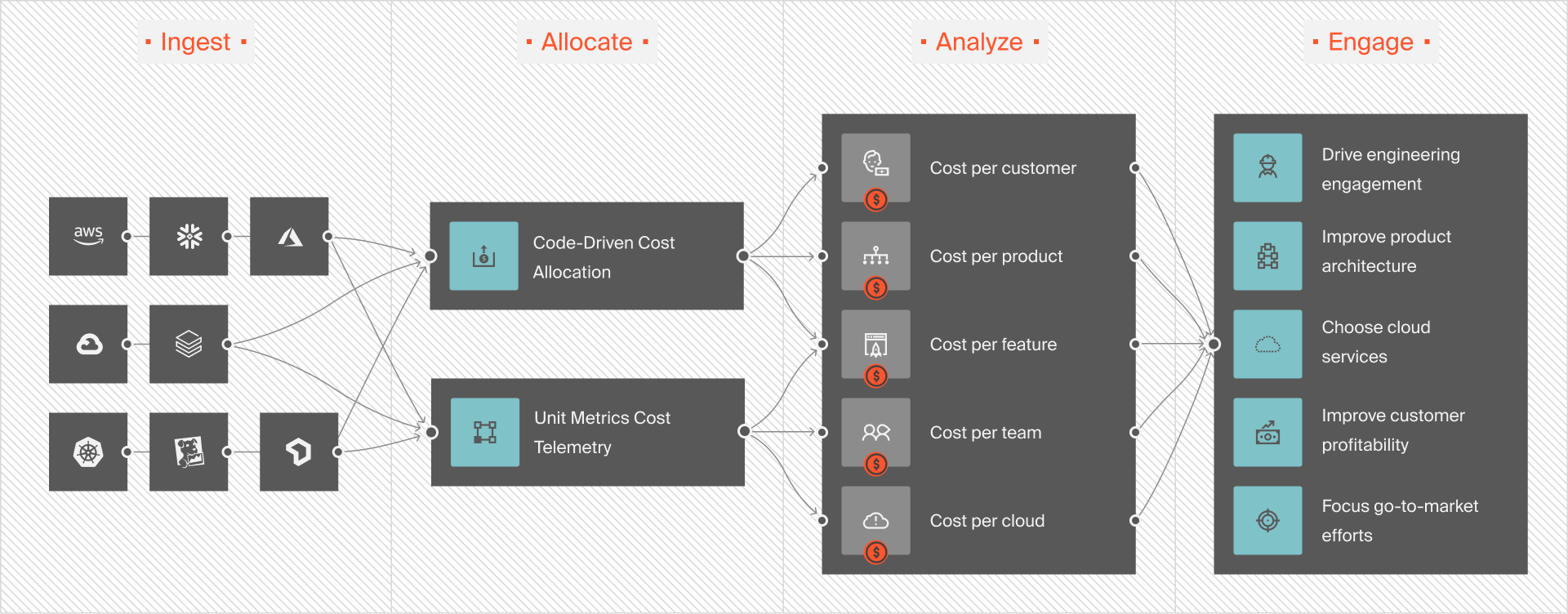
From Terraform to Pulumi to Crossplane, we make cloud cost visibility as programmable as your code.
And you won’t be doing it alone. High-performing teams at Skyscanner, Duolingo, Remitly, and Moody’s already use CloudZero to align infrastructure decisions with business impact (and prevent six-figure billing surprises).
If you’re evolving your IaC strategy, now is the time to upgrade your cost visibility too. Don’t wait for next month’s bill to find out what went wrong.  and see how CloudZero delivers clarity where it counts.
and see how CloudZero delivers clarity where it counts.