A SaaS team once spotted their first breach not in a SIEM dashboard, but in their AWS bill. Their compute costs spiked by 400% overnight. Turns out, an attacker had spun up dozens of high-powered instances for crypto mining. Logs eventually confirmed the intrusion, but the cost anomaly was the first signal that something was wrong.
This incident isn’t unusual. Cloud costs often reflect consumption, but they can also reflect compromise.
That’s why cloud cost monitoring for security, or cost monitoring for cloud security, is no longer just a FinOps concern. It’s a proactive defense strategy you can add to your DevSecOps strategy.
In this post, we’ll unpack how cost monitoring for cloud security works, the risks cost anomalies can reveal, and how forward-looking teams use platforms like CloudZero to align cost accountability with security.
What Does Cloud Cost Monitoring For Security Involve?
This approach bridges financial efficiency and operational resilience. It points to treating cloud spend data as part of your first-class security telemetry. Just as you’d track CPU utilization or audit logs, you can also monitor financial signals that reveal suspicious or unauthorized activity.
Here are some key elements involved in cost monitoring for cloud security:
- Real-time visibility into your spend enables you to detect cost anomalies within minutes, not weeks, even when the bill is already bloated.
- Cost anomaly detection (using machine learning or rule-based thresholds) highlights sudden spikes in compute, storage, or data transfer fees that don’t match your historical patterns. This often forms the “smoke alarm” for cost-driven threats.
- Integration with incident response: Cost anomalies should feed directly into your SOC or SIEM alongside logs and performance alerts. This way, your security folks can triage spikes immediately rather than relying on finance teams to notice them later.
- Cross-team accountability via access controls: Insights such as cost per deployment and cost per environment should not only live in finance dashboards, but also within DevSecOps.
- Treating costs as first-class security telemetry also creates a paper trail for auditors, helping your teams prove accountability.
Let’s see how this works.
How Cost Spikes Can Reveal Security Risks
Attackers leave financial traces when they misuse cloud resources, sometimes hours or even days before traditional alerts kick in.
Here are some common scenarios where cloud cost monitoring for security surfaces hidden risks:
- Unauthorized resource provisioning: A compromised account spins up dozens of high-powered VMs for, say, crypto mining. Your bill skyrockets overnight, long before system performance metrics look unusual.
- Large-scale data exfiltration: If attackers move sensitive data out of your environment, you’ll often see it first as a spike in outbound (egress) transfer costs.
- Abnormal API activity: Bots or unauthorized integrations may hammer your APIs, leading to inflated request charges and unusual traffic patterns.
- Idle but costly workloads: Malicious actors sometimes deploy resources and leave them running in silence. These don’t always trigger operational alarms, but they show up clearly as unexplained spend.
The real power comes when you correlate these anomalies with operational and security logs. For example:
A spike in compute spend, combined with login activity from an unfamiliar region, could confirm a compromised account.
A sudden jump in storage, together with unexpected API calls, could point to bulk data downloads.
By integrating cost signals into your broader incident response, you can act without waiting for logs or user alerts. You can spot trouble through the one metric attackers can’t hide — the bill.
However, not every bump in your cloud bill signals a breach. So, what metrics should you keep an eye on?
Use These Key Cloud Cost Metrics (And Indicators) To Catch Security Issues In The Cloud
Certain patterns should immediately catch your attention because they map directly to risk:
- Sudden increases in compute or storage costs: May point to unauthorized provisioning, crypto-mining, or runaway workloads.
- Unexpected spikes in data transfer (egress): Large outbound traffic, especially to regions you don’t usually operate in, could indicate data exfiltration.
- Resources running without associated workloads can reveal forgotten or malicious deployments.
- Geographic anomalies: Spend suddenly appearing in regions you don’t use may flag unauthorized activity or misconfigured services.
- Unusual API or service charges: Abnormal consumption of API calls, serverless functions, or third-party services often correlates with bot traffic or unauthorized integrations.
Also see:
And as we’ve mentioned before, you’ll want to correlate these anomalies with operational and security telemetry.
For example, link a spike in compute spend to login data, or match unexpected egress costs to IAM audit logs. This correlation reduces false positives and helps your teams confirm whether a spike is benign (like a marketing campaign gone viral) or malicious (like an ongoing breach).
By watching the right cost signals, you can turn billing data into a frontline security tool, one that complements traditional logs, metrics, and alerts — and bolsters your incident response.
Cost Accountability: The Overlooked Way To Improve Your Cloud Security Posture
Security has always been about visibility: knowing what’s happening in your systems, where risks live, and how to contain them. But that visibility has often stopped at logs and metrics. Adding cost accountability into the mix closes that gap. Here’s how:
Detect breaches early
Cost anomalies, especially if you are using real-time cloud cost analysis, often surface before logs raise alarms. By holding teams accountable for unexplained spikes, you shorten the time it takes to detect and respond to threats.
Surface issues with cross-team collaboration
When finance, engineering, and security share a common cost view, your investigations become faster and more precise. A sudden egress spike becomes an immediate security conversation.
Shift toward shared responsibility
When every team is responsible for the spend tied to their workloads, cost becomes a natural extension of DevSecOps. Security isn’t siloed anymore, but it’s baked into how you use and justify resources.
Protect profitability and resilience
Stronger security also protects margins. Unchecked security gaps drive real financial losses. Embedding cost monitoring into your cybersecurity arsenal ensures you can reduce risks and protect your margins.
Related reads:
Let’s get into how to actually do that below.
How To Embed Cost Accountability Into Your Incident Response Workflows
Embedding this approach into your response playbook means you’re not waiting for an invoice to tell you something went wrong. You’re catching issues while they happen, minimizing both breach impact and financial damage.
Here’s how we see leading SaaS teams do it:
- Detect: Real-time monitoring surfaces a cost anomaly, such as a spike in compute spend or sudden outbound transfer charges.
- Validate: The anomaly routes into your SOC or SIEM, where it’s triaged alongside logs, metrics, and alerts. Security teams cross-check the spike against IAM activity, API logs, or region-level usage.
- Escalate: If the anomaly points to suspicious activity, a ticket is opened in your favorite incident management platform (PagerDuty, Jira, ServiceNow, etc.).
- Investigate and remediate: Engineering and security collaborate to isolate the affected resource, revoke compromised credentials, or shut down rogue workloads.
- Analyze and learn: Post-incident reviews include cost anomaly data. Teams ask questions like, “What cost did we manage to avoid here?”, “How fast did we detect it?”, and “Can we tune thresholds or alerts to catch issues sooner?”
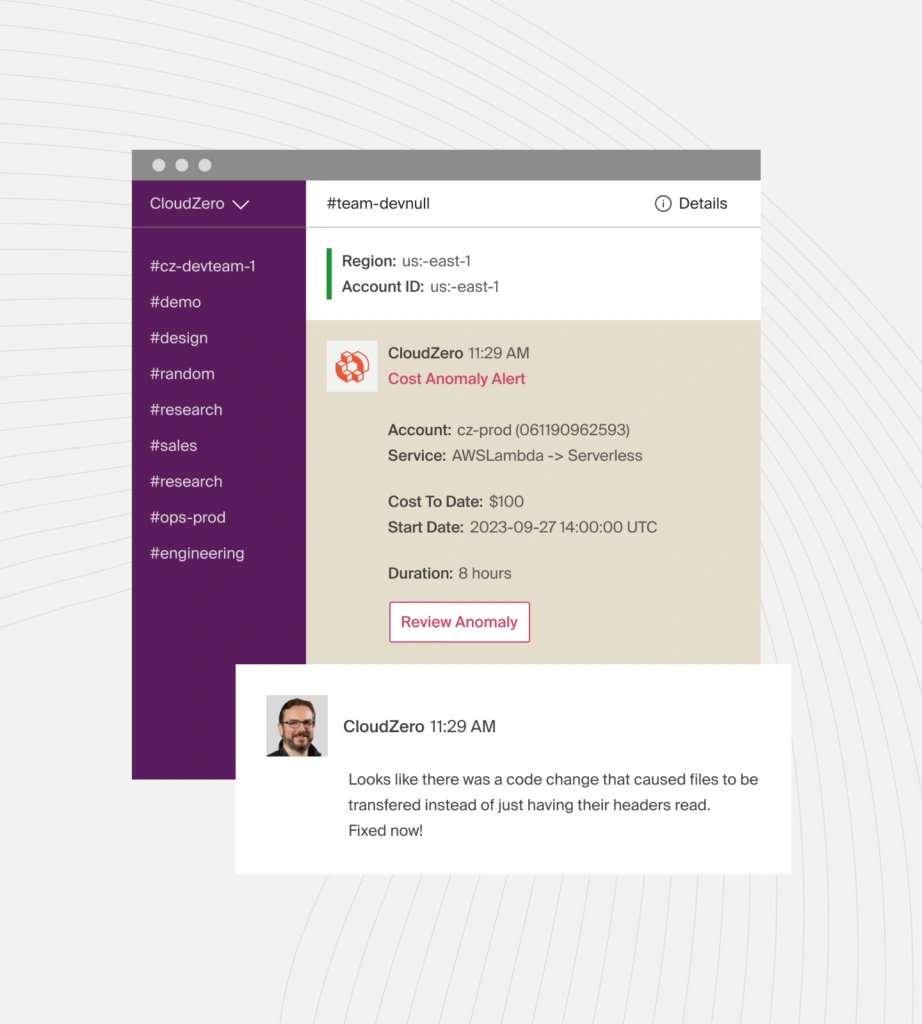
This workflow transforms your spend data into an operational security signal. And with modern RBAC and context-driven alerts, solutions like CloudZero can help you ensure cost anomalies don’t overwhelm finance or security teams with noise.
Related read: How These User Groups Unlock Modern RBAC For Contextual Cloud Cost Optimization
Instead, they can feed the right signals to the right people at the right time to protect your bottom line. Here’s how.
Turn Cloud Costs Into Your Strongest Security Signal Yet
In most organizations, a sudden cost spike is first seen as a budgeting problem. But in many cases, it’s actually the earliest signal of a security incident. Yet, most cloud cost tools stop at just monitoring waste.
CloudZero goes further. Instead of just tracking spend, we deliver context-rich intelligence that turns your costs into a security signal.
With CloudZero, you can:
- Break down 100% of your spend by environment, feature, deployment, and more unit-level insights, so when a suspicious spike occurs, you know exactly who, when, and where to engage.
- Get shared accountability by surfacing costs to the teams responsible for them, aligning engineering, security, and finance.
- Keep access secure with modern RBAC controls that give security teams visibility into anomalies without exposing sensitive financial data.
- Catch threats early with AI-powered anomaly detection that learns your “normal” spend and alerts the right people when it spikes.
And we’re not the only ones who trust this approach. Cybersecurity leaders such as MalwareBytes, Forcepoint, Obsidian Security, and Rapid7 all use CloudZero to monitor and optimize their own internal cloud costs. Any organization building in the cloud can use this approach.
But don’t just take our word for it.  and see how CloudZero acts as your early-warning system, protecting both your workloads and margins.
and see how CloudZero acts as your early-warning system, protecting both your workloads and margins.